d888888o. 8888888 8888888888 8 8888888888 ,o888888o. .8. b. 8 ,o888888o. ,o888888o. 8 888888888o. .8. 8 888888888o 8 8888 8 `8.`8888. ,8' .`8888:' `88. 8 8888 8 8888 8888 `88. .888. 888o. 8 . 8888 `88. 8888 `88. 8 8888 `88. .888. 8 8888 `88. 8 8888 8 `8.`8888. ,8' 8.`8888. Y8 8 8888 8 8888 ,8 8888 `8. :88888. Y88888o. 8 ,8 8888 `8b ,8 8888 `8. 8 8888 `88 :88888. 8 8888 `88 8 8888 8 `8.`8888. ,8' `8.`8888. 8 8888 8 8888 88 8888 . `88888. .`Y888888o. 8 88 8888 `8b 88 8888 8 8888 ,88 . `88888. 8 8888 ,88 8 8888 8 `8.`8888.,8' `8.`8888. 8 8888 8 888888888888 88 8888 .8. `88888. 8o. `Y888888o. 8 88 8888 88 88 8888 8 8888. ,88' .8. `88888. 8 8888. ,88' 8 8888 8 `8.`88888' `8.`8888. 8 8888 8 8888 88 8888 .8`8. `88888. 8`Y8o. `Y88888o8 88 8888 88 88 8888 8 888888888P' .8`8. `88888. 8 888888888P' 8 8888 8 `8. 8888 `8.`8888. 8 8888 8 8888 88 8888 8888888 .8' `8. `88888. 8 `Y8o. `Y8888 88 8888 ,8P 88 8888 8888888 8 8888`8b .8' `8. `88888. 8 8888 8 8888888888888 `8 8888 8b `8.`8888. 8 8888 8 8888 `8 8888 .8'.8' `8. `88888. 8 `Y8o. `Y8 `8 8888 ,8P `8 8888 .8' 8 8888 `8b. .8' `8. `88888. 8 8888 8 8888 8 8 8888 `8b. ;8.`8888 8 8888 8 8888 8888 ,88'.888888888. `88888. 8 `Y8o.` ` 8888 ,88' 8888 ,88' 8 8888 `8b. .888888888. `88888. 8 8888 8 8888 8 8 8888 `Y8888P ,88P' 8 8888 8 888888888888 `8888888P' .8' `8. `88888. 8 `Yo `8888888P' `8888888P' 8 8888 `88. .8' `8. `88888. 8 8888 8 8888 8 8 8888
A quick introduction to steganography and a proposal to the Voice Processing course group project.
Definition
As seen in [1]:
Steganography and steganalysis are important topics in information hiding. Steganography refers to the technology of hiding data into digital media without drawing any suspicion, while steganalysis is the art of detecting the presence of steganography.
And on Wikipedia:
Steganography is the practice of concealing a file, message, image, or video within another file, message, image, or video. The word steganography combines the Greek words steganos, meaning "covered, concealed, or protected," and graphein meaning "writing".
CRYPTOGRAPHY
Steganography focuses on the concealment of the fact that the message is beign sent as well as concealing its content.
Considering the example below, which would be more likely to be ignored in a monitored medium, the cipher text or the image?
HELLO WORLD
AYE4jnEpKaYsuDE=
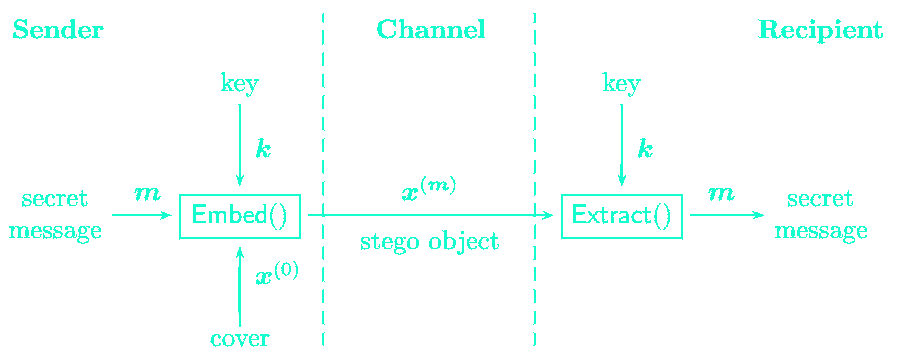
Modeling
Steganography can be modeled as the prisioner's problem. Two steganographers communicating covertly over a public channel take the hole of the prisoners as agent(s) monitor the channel.
Evaluating
What makes steganography good?

How easily the existence of steganography can be estimated

How much information can be stored in a message

How much perceptible distortion or noise was generated
Stego Objects
Steganography can be applied to any medium.
- written text
- hairstyles
- clothing
- body movements
- ...
- digital text
- media encoding
- mimic functions
- content manipulation
- ...
- puzzles
- naming of things
- networks
- intentional mistakes
- ...
There is a lot of research and interest in digital media. In this work, we'll be looking at digital audio.
AUDIO FILE FORMATS
As in any type of data file, audio files can be found in different types and sizes. In regards to steganography, compression is one of the most importants aspects.
- WAV
- AIEF
- ...
- Mp3
- WMA
- ...
- ALAC
- FIAC
- ...
Different types of compression require different types of steganographic methods, and may cause destructive interference on the retrieval of hidden information. Such is the case, that resistance to compression may be considered an important evaluation metric, which falls in the capacity of the steganographic method.
THE WAVE FORMAT
For this project, we will work with the WAVE (Waveform Audio File Format) file format, which is easy to work with and has widespread adoption.

- Uncompressed, generating large files
- Simple structure
- One of the most popular audio formats
- Windows default audio format
- Developed by Microsoft and IBM
- .wav file name extension
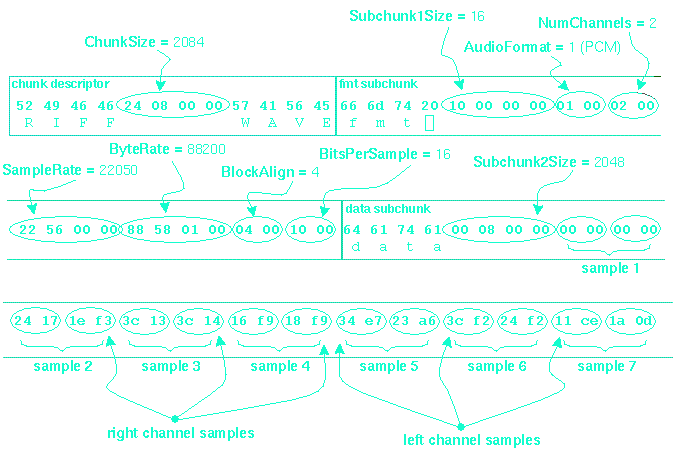
THE WAVE FORMAT [2][3]
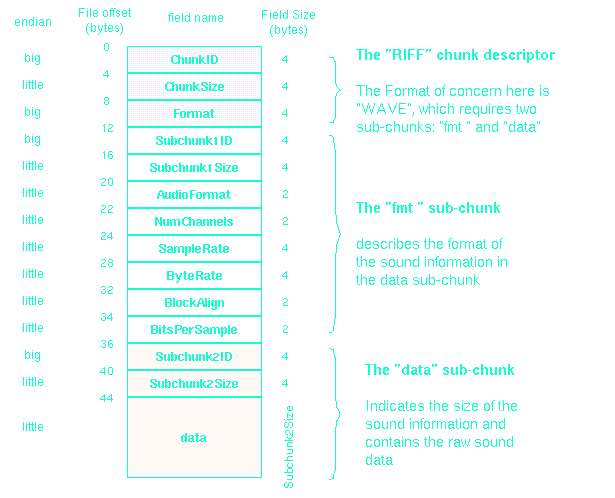
THE WAVE FORMAT [2][3]
PROJECT: LSB WAVE STEGANOGRAPHY TOOL

The group proposal for the course project consists in the creation of an easy to use steganography tool for .wav audio files, using the LSB steganographic method.
The LSB method is one of the most simple steganographic methods, and is very suitable for the WAVE format due to it being an uncompressed format of very simple structure.
If successfull at the LSB method, the project also aims at studying and implementing different methods of steganography, such as the Spread Spectrum [4], which hides the data in the frequency domain, similar to 2D DCT steganography in images.
8888888 8888888888 8 8888 8 .8. b. 8 8 8888 ,88' d888888o.
8 8888 8 8888 8 .888. 888o. 8 8 8888 ,88' .`8888:' `88.
8 8888 8 8888 8 :88888. Y88888o. 8 8 8888 ,88' 8.`8888. Y8
8 8888 8 8888 8 . `88888. .`Y888888o. 8 8 8888 ,88' `8.`8888.
8 8888 8 8888 8 .8. `88888. 8o. `Y888888o. 8 8 8888 ,88' `8.`8888.
8 8888 8 8888 8 .8`8. `88888. 8`Y8o. `Y88888o8 8 8888 88' `8.`8888.
8 8888 8 8888888888888 .8' `8. `88888. 8 `Y8o. `Y8888 8 888888< `8.`8888.
8 8888 8 8888 8 .8' `8. `88888. 8 `Y8o. `Y8 8 8888 `Y8. 8b `8.`8888.
8 8888 8 8888 8 .888888888. `88888. 8 `Y8o.` 8 8888 `Y8. `8b. ;8.`8888
8 8888 8 8888 8 .8' `8. `88888. 8 `Yo 8 8888 `Y8. `Y8888P ,88P'
References:
[1] A survey on image steganography and steganalysis. Journal of Information Hiding and Multimedia Signal Processing, 2(2), 2011. By Jiwu Huang, Yun Qing Shi, Bin Li, Junhui He
[2] WAVE Audio File Format, Library of Congress
[3] WAVE PCM soundfile format, soundfile++: A Soundfile Reading/Writing Library in C++
[4] Hiding Data in Wave Files.International Conference in Recent Trends in Information Technology and Computer Science (ICRTITCS - 2012). By Pushpa Aigal, Pramod Vasambekar.