CryptoStego - YASS Version
This project is a fork of Jeffery Zhaos's
CryptoStego project, which implements well known
steganographic methods and cryptography to hide and protect text in images.
This fork implements a new steganographic method, inspired by the YASS method.
The implementd method consists of hiding the data inside the 2D Discrete Cosine Transform
results of pseudo-randomly spatially located 8x8 blocks of the image. More info on the method
is available at the About section below.
Parameters
Note that the same parameters used to hide a message must be used to recover it!
- Level 0: [Copies:5][Limit:30] - Best Secrecy, No Robustness to Compression
- Level 1: [Copies:11][Limit:15] - (Warning: This level has very low data capacity)
- Level 2: [Copies:9][Limit:20]
- Level 3: [Copies:5][Limit:30]
- Level 4: [Copies:5][Limit:35]
- Level 5: [Copies:5][Limit:50] - Best Robustness to Compression, Worst Secrecy
** B size is the outer B block size used by the YASS method.
Hide a Message
Security Password:
Recover a Message
Security Password:
Results:
About
This project uses the CryptoStego framework/library created by Jeffery Zhaos to implement a new steganographic method, greatly inspired by the YASS method, which was proposed in the article:
Solanki, K & Sarkar, Anindya & Manjunath, B. (2007). YASS: Yet Another Steganographic Scheme That Resists Blind Steganalysis. Lect Notes Comput Sci. 2939. 16-31. 10.1007/978-3-540-77370-2_2.
If you have interest in this subject, I highly suggest you to take a look at the article, as this implementation is not really faithful to the article proposal. The following images show the basic idea behind the steganographic methos in this project, the first beeing the standard 2D DCT data hiding and the second the new method. Both hide the data changing the lowest frequency component of each block, resulting in distorted images.

2D DCT data hiding in 8x8 JPEG blocks
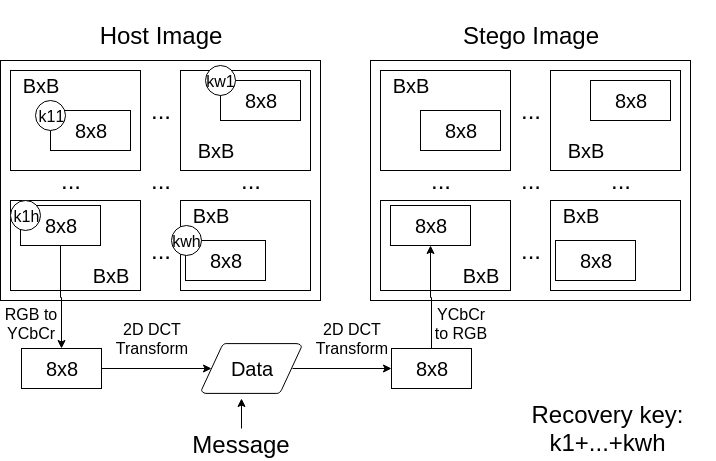
YASS inspired data hiding
As mentioned, both methods generate distorted images. Below are some comparisons of the results obtained by each method, using the robustness level 0, described at the Parameters section.

The original JPEG image

The image resulting from the standard DCT method, at the robustness level 0, hiding the text "hey there", with password "123".

The image generated by the YASS inspired method, for the same parameters, message and password as before, and B size equals 11.
The generated distortion is clear for both cases, as it is usual for frequency Transform methods used for image and video compression. For the second image, we can also see the many smaller 8x8 blocks inside the BxB blocks. By varying the robustness level, we can get quite distinct results.

Robustness level 5 and B size equals 11. High compression robustness, low secrecy.

5 copies, limit 10 and B size equals 11. Low compression robustness, high secrecy.
We can also decrease the B size paramenter, i.e., the outer block size. It can only be as small as 8, in which case the method becomes the same as the usual DCT steganographic method. As B increases, the hiding capacity decreases, as the message is only written inside the 8x8 inner blocks.

Robustness level 0, B size 8

Robustness level 0, B size 16